Always Check The Default Parameters When Assigning An Azure Policy
This week I was helping a colleague with troubleshooting an Azure policy deployment that appeared successful but wasn’t taking effect, and I thought I’d share a tip with you that I passed on during the process.
The Problem
A colleague approached me as they were having issues with a policy not deploying diagnostic settings to a Network Security Group (NSG) and asked if I could take a look. They were using the portal to assign a policy for testing, and explained exactly the process they gone through which resulted in the deployment taking place but no settings getting applied.
The Policy
The policy in question was a BuiltIn policy provided by
Microsoft
named Enable logging by category group for Network security groups (microsoft.network/networksecuritygroups) to Event Hub. This was the correct policy to choose, as the requirement was to send all available logs to an Event Hub for processing.
The Assignment
When assigning the policy you are presented with the Basics tab where you specify the scope of the assignment and any exclusions etc, then you proceed to the Parameters tab as per below.
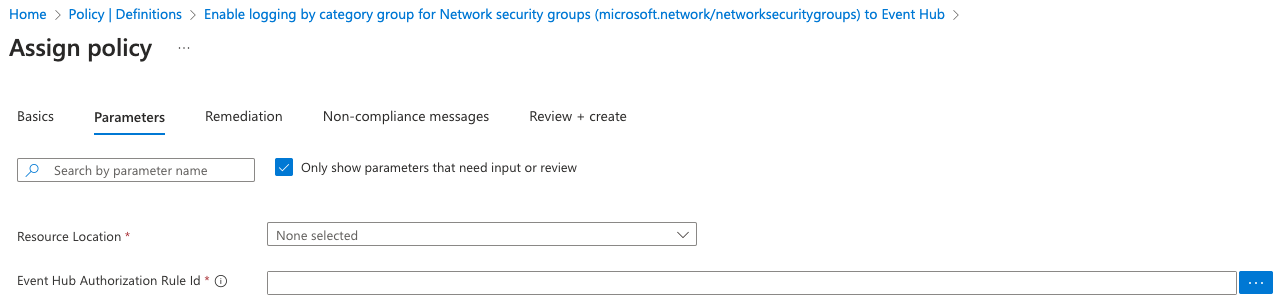
You can see that you are only prompted for 2 parameters, Resource Location and Event Hub Authorization Rule Id. I don’t have an Event Hub in my subscription, so I have this this blank just to show you the process. Both of these had been correctly specified and the policy was assigned but no settings were applied.
The Available NSG Diagnostic Settings
We headed over to the NSG resource to see exactly what settings were available:
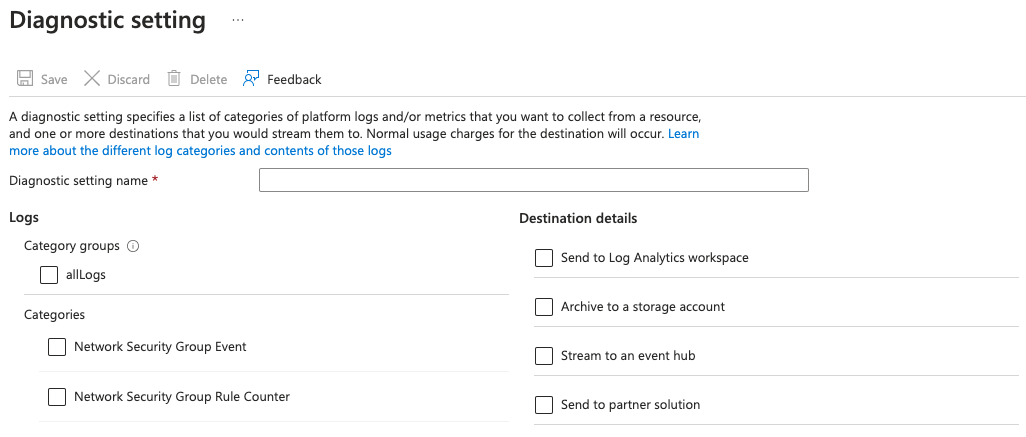
You can see there are not many options to select from, and there is only a single Category Group named allLogs.
The Solution
We went back to the policy assignment and this time unchecked the Only show parameters that need input or review box.
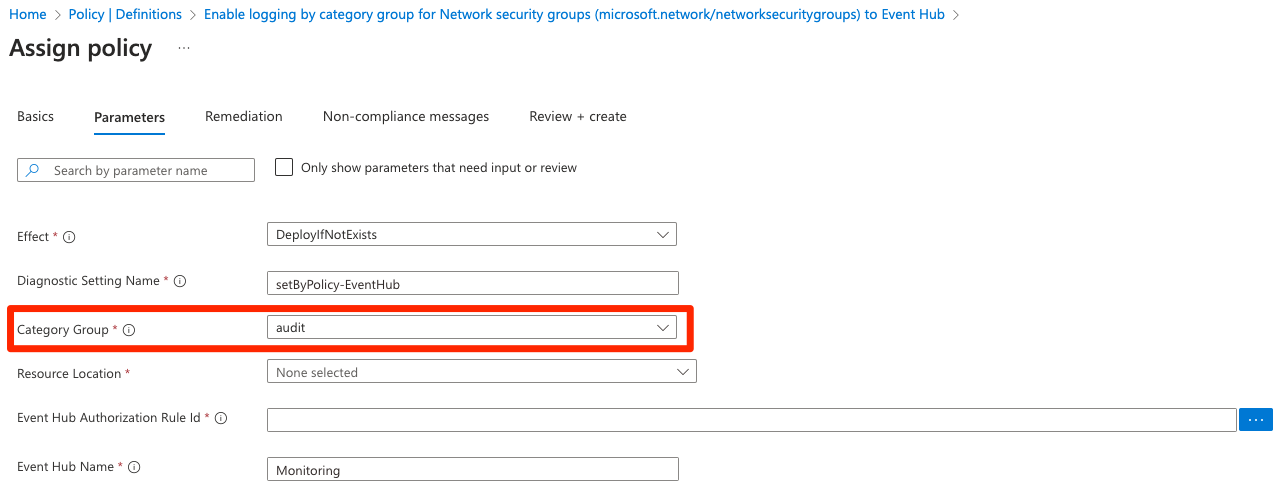
Now you can see there are now an additional 4 parameters available. These were hidden away as their default value had been set in the policy, and was not required in order to complete the assignment. The root of the problem here was that the Category Group was set as audit by default and there is no Category Group named audit even available for the NSG diagnostics! We amended this to allLogs and reassigned the policy and waited for the deployment to complete. This time the diagnostic settings were applied as desired.
Reporting The Problem
I knew as this was a BuiltIn policy other Azure customers could experience this same problem and the
documentation
said to open an issue or a support ticket. I didn’t see the value in opening a support ticket, so I have logged an issue for it on GitHub
here
. I’ll be interested to follow this and see what happens.
Key Takeaway: Always check the default options are correct and align to what you are trying to achive when assigning a new policy for the first time as Azure is constantly evolving and settings are being deprecated all the time.
